Bloom Cyber Security Summary
Bloom Cyber Security Summary
Overview
Cyber security and compliance are top priorities at Bloom; they are a fundamental aspect of our product’s developer experience. Bloom is committed to protecting our clients data, and that of the consumers they serve, through a combination of employee training, automated policy checks embedded within the DevOps lifecycle, and regular scanning, testing, and auditing.
As an AWS customer, we have implemented technology solutions and controls to ensure we are adhering to industry best practice in regards to the security and protection of all customer responsibilities in the shared responsibility model. Configurations are verified against industry best practices for the technologies used.
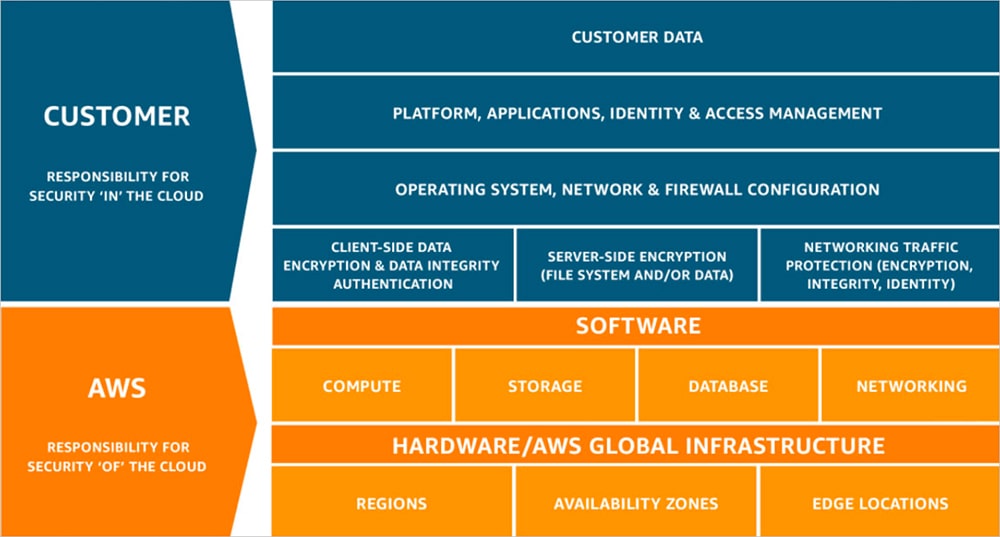
Infrastructure and Network Security
The Bloom platform is hosted at AWS, whose data centers have extensive physical security controls, documented by AWS and affirmed by their auditors.
All infrastructure provisioned at AWS is done so using Infrastructure-as-Code managed by a platform with support for the Open Policy Agent to ensure adherence with standards and best practices, including a default DENY ALL access policy for all resources.
Bloom has adopted a zero-trust architecture for privileged access to the internal network and infrastructure, and leverages a privileged access management system to ensure that all access is approved and logged.
All data is encrypted both in transit and at rest within the Bloom environment. Regular scanning is performed to ensure that no untokenized sensitive data is stored within the environment.
The Bloom platform runs across multiple availability zones in AWS, with database backups stored in a separate account in a different region. A second region is configured as a pilot light, with the ability to apply terraform and create necessary infrastructure. The DR plan is walked through on an annual basis to ensure all necessary steps are accounted for.
Cloud environments are protected with a cloud IDS, and anti-malware solutions. All logs and events are aggregated and funneled to an SIEM platform configured to alert on threats within the MITRE ATT&CK framework. Bloom engineers respond to security alerts at all times.
Application Security
Application security at Bloom starts with regular training for all software engineers on secure coding practices. As part of the CI/CD process, all code is checked for vulnerabilities using a static code analysis tool. Confirmed Critical or High vulnerabilities are remediated before deployment to production.
Client’s interact with the Bloom platform using TLS 1.2 encrypted connections, and authenticate all requests using JWT tokens. In addition to encrypting all data at rest and in motion, Bloom takes the additional step of tokenizing all sensitive consumer PII to reduce the risk of unintended or unauthorized disclosure.
Web application scanning and penetration testing are performed on a regular cadence. Remediation is prioritized based on finding severity. Mitigating controls are added as necessary.
Corporate Security
Company-issued user equipment is centrally managed and configured to a consistent standard including full-disk encryption, malware prevention, data loss monitoring, and remote wipe capabilities.
Vendor management is performed via a due diligence process with security capability verification for high-risk vendors.
Employee access to systems is managed centrally using an Identity Provider platform with MFA and posture enforcement capabilities. Access is granted based on role, or on an exception basis with logged approval from the employee’s manager and the system owner. Access levels are reviewed on a quarterly basis to ensure that employees only have access to systems as required by their job duties.
Employee Security
Employee security measures include background verification, annual security awareness, and confirmation of policy acceptance. There is department specific training such as developer security training for coding best practices, and education requirements for security personnel relevant to their certifications. Periodic verification of training is performed via phishing/social engineering testing.
Security personnel are qualified and certified including CISSP, CISA, CDPSE, and Security+ certifications.
Disclosure Policy
In accordance with client contract and applicable laws, Bloom will notify involved parties in the event of a confirmed or suspected breach of personal information. Bloom will engage law enforcement and additional resources as necessary.